Cloud Migration Security: How To Build A Secure And Scalable Cloud Migration Strategy

Cloud migration security has become a top priority for organizations moving applications and data to the cloud. While cloud platforms offer flexibility, scalability, and faster innovation, insecure migrations can expose sensitive data, disrupt operations, and create long-term compliance challenges.
A secure cloud migration requires more than moving workloads from on premises environments to cloud platforms. It demands a clearly defined cloud migration security strategy that protects identities, applications, and data across every phase of the migration lifecycle.
This guide explains cloud migration security, explores why cloud migration data security is critical, and outlines practical steps organizations can follow to enable a secure cloud migration with confidence.
What Is Cloud Migration Security
Cloud migration security refers to the processes, controls, and technologies used to protect systems, workloads, and data before, during, and after migration to the cloud.
Cloud environments operate under a shared responsibility model. Cloud service providers secure the underlying infrastructure, while organizations are responsible for securing configurations, identities, applications, and data.
Cloud migration data security focuses specifically on protecting sensitive information as it moves between environments. This includes encryption, access control, monitoring, and policy enforcement to prevent unauthorized access or data loss.
Why Cloud Migration Security Is Critical for Modern Enterprises
As organizations adopt cloud services, the attack surface expands significantly. Without strong cloud migration security, misconfigurations, weak identity controls, and lack of visibility can lead to data breaches and service disruptions.
Key reasons cloud migration security is critical include increased exposure of internet facing services, limited visibility across hybrid and multi cloud environments, strict regulatory compliance requirements, and the growing sophistication of cloud based threats.
A secure cloud migration protects business operations while maintaining customer trust and regulatory alignment.
Cloud Migration Security Strategy for Enterprises
A successful cloud migration security strategy begins before workloads are migrated and continues throughout cloud operations.
1. Define Ownership and Responsibility
Clear accountability ensures that teams understand their role in managing cloud migration security across infrastructure, applications, and data.
2.Classify and Prioritize Data
Identifying sensitive data early helps define appropriate security controls, encryption requirements, and access policies aligned with business risk.
3.Design Secure Cloud Architecture
Security should be embedded into cloud architecture using identity driven access controls, network segmentation, logging, and monitoring by default.
4.Automate Security Controls
Automation reduces human error and ensures consistent enforcement of cloud migration security policies at scale.
Secure Cloud Migration: Step-by-Step Approach
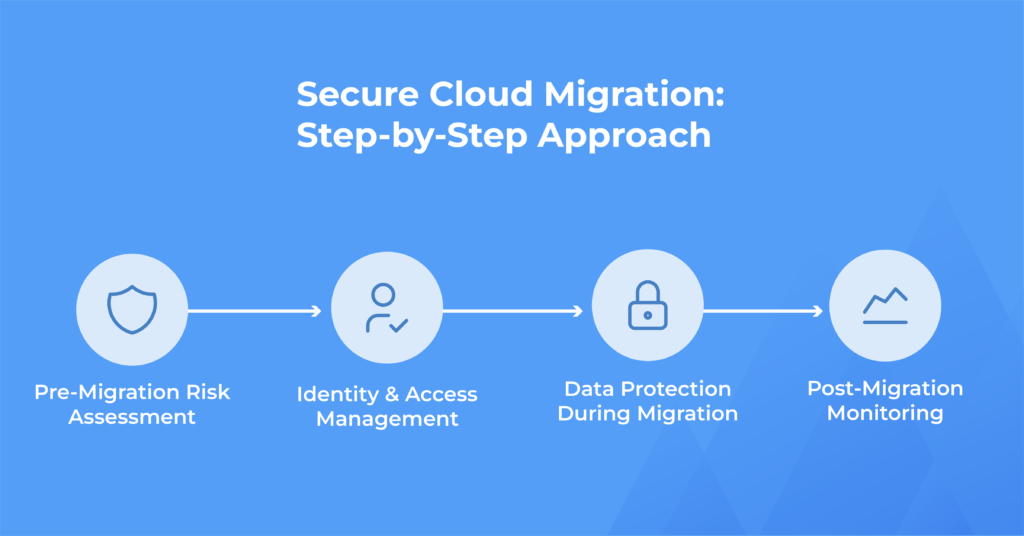
A secure cloud migration follows a structured and security first approach rather than a simple lift and shift model.
1.Pre Migration Risk Assessment
Organizations must assess workloads, dependencies, vulnerabilities, and compliance requirements to identify risks before migration begins.
2.Identity and Access Management
Strong identity and access management ensures that only authorized users and services can access cloud resources using least privilege principles.
3.Data Protection During Migration
Cloud migration data security requires encrypting data in transit and validating data transfers to prevent unauthorized access or data exposure.
4.Post Migration Monitoring
Continuous monitoring enables organizations to detect misconfigurations, policy violations, and suspicious activity in real time.
Cloud Migration Data Security Best Practices
Protecting data is a core pillar of cloud migration security.
1.Encrypt Data at All Stages
Encryption should be applied to data at rest, in transit, and where possible during processing to reduce exposure risk.
2.Restrict Access to Sensitive Information
Access to sensitive data must be limited based on business needs and reviewed regularly to prevent excessive permissions.
3.Monitor Data Movement
Visibility into data flows across cloud services helps prevent unauthorized access and data exfiltration.
4.Align With Compliance Requirements
Cloud migration data security must support regulatory frameworks such as GDPR, HIPAA, or PCI DSS to avoid compliance violations.
Cloud Migration Security Checklist for Risk Reduction
A cloud migration security checklist helps teams apply consistent security controls throughout the migration process.
• Define shared responsibility roles
• Implement identity and access controls
• Encrypt data in transit and at rest
• Secure APIs and application endpoints
• Enable centralized logging and monitoring
• Validate configurations after migration
• Continuously assess security posture
Common Cloud Migration Security Challenges
Many organizations encounter cloud migration security challenges due to complexity and lack of preparation.
Misconfigurations remain the most common cause of cloud security incidents. Limited visibility, fragmented security tools, and skills gaps further increase risk.
Addressing these challenges requires cloud native security tools, continuous monitoring, and governance aligned with cloud environments.
Why Many Cloud Migrations Fail Security Reviews
Cloud migrations often fail security reviews because security is introduced too late. Reusing legacy security models and lacking real time visibility increases exposure to threats.
Cloud migration security must evolve continuously to support changing workloads, architectures, and threat landscapes.
From Cloud Adoption to Cloud Security Maturity
As organizations mature, cloud migration security shifts from basic controls to proactive risk management. Mature security programs focus on continuous visibility, automated remediation, and policy driven governance.
When security is embedded into cloud operations, it enables innovation rather than restricting it.
Design and Implement Secure Cloud Migration Solutions
A successful cloud migration depends on how well security is planned and executed. We help organizations design and implement cloud migration security strategies that protect data, applications, and identities from day one.
Whether you are planning your first migration or strengthening an existing environment, our secure cloud migration solutions focus on risk reduction, compliance, and long-term scalability. Partner with us to enhance cloud migration data security and migrate with confidence.
Frequently Asked Questions
What is cloud migration security and why is it important?
Cloud migration security protects systems and data during and after migration to the cloud and ensures workloads remain secure and compliant.
Who is responsible for cloud migration security?
Cloud providers secure infrastructure, while organizations are responsible for securing identities, configurations, applications, and data.
How can organizations ensure cloud migration data security during migration?
Organizations ensure cloud migration data security by encrypting data, controlling access, monitoring activity, and enforcing security policies consistently.
Is cloud migration more secure than on premises environments?
Cloud environments can be highly secure when configured correctly and managed using strong cloud migration security practices.
Contact us to learn how our cloud migration security solutions help organizations secure data, manage access, and maintain visibility throughout the cloud migration lifecycle.